Ensuring Compliance: The Role of User Access Reviews in Data Security
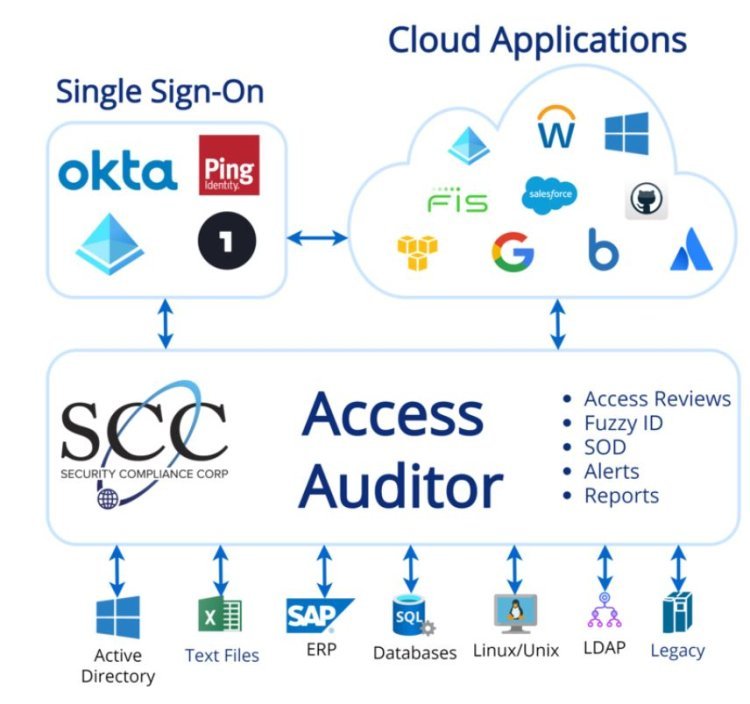
Introduction:
In today's digital age, data security is a top priority for organizations across industries. With the increasing volume of sensitive information stored and transmitted electronically, ensuring the confidentiality, integrity, and availability of data has become paramount. User access reviews play a critical role in data security by helping organizations maintain control over who has access to sensitive data and ensuring compliance with regulatory requirements. In this article, we'll explore the importance of user access reviews in data security and their role in ensuring compliance with relevant regulations and standards.

Understanding User Access Reviews:
User access reviews, also known as access recertifications or entitlement reviews, are periodic assessments conducted to verify and validate the access rights assigned to users within an organization. These reviews involve examining user permissions, roles, and entitlements to ensure that they align with the principle of least privilege – granting users only the permissions necessary to perform their job functions. By conducting regular access reviews, organizations can identify and address inappropriate access, reduce the risk of data breaches, and maintain compliance with regulatory requirements.
The Role of User Access Reviews in Data Security:
User access reviews play a crucial role in data security by helping organizations:
- Identify and Mitigate Access Risks: Regular access reviews enable organizations to identify and mitigate security risks associated with excessive or inappropriate access rights. By reviewing user permissions and entitlements, organizations can ensure that access controls are properly configured and aligned with business needs, reducing the risk of unauthorized access and data breaches.
- Enforce Segregation of Duties (SoD): User access reviews help enforce segregation of duties (SoD) controls by identifying conflicts of interest or incompatible access rights that could lead to fraud or abuse. By reviewing user roles and permissions, organizations can ensure that no single user has the ability to perform conflicting actions that could compromise data integrity or security.
- Maintain Compliance: Many regulatory frameworks and industry standards require organizations to implement controls for managing user access and enforcing segregation of duties. User access reviews help organizations demonstrate compliance with these requirements by providing evidence of ongoing access control assessments and remediation efforts. By conducting regular access reviews, organizations can ensure that access controls remain effective and compliant with regulatory requirements.
- Enhance Incident Response: User access reviews provide valuable insights into user activity and behavior, which can help organizations detect and respond to security incidents more effectively. By monitoring user access patterns and identifying anomalies or suspicious activity, organizations can mitigate the impact of security breaches and prevent unauthorized access to sensitive data.
Key Considerations for Effective User Access Reviews:
To ensure the effectiveness of user access reviews in data security and compliance, organizations should consider the following key factors:
- Establish Clear Policies and Procedures: Define clear guidelines, policies, and procedures for conducting user access reviews, including roles and responsibilities, review frequency, review scope, and documentation requirements. Communicate access review requirements to relevant stakeholders and ensure that they understand their roles and responsibilities in the review process.
- Leverage Technology Solutions: Invest in access management and identity governance solutions that automate access review workflows, streamline review processes, and provide visibility into user entitlements and access rights. By leveraging technology solutions, organizations can conduct access reviews more efficiently, accurately, and consistently.
- Conduct Regular Reviews: Establish a regular cadence for conducting access reviews, such as quarterly or annually, to ensure that access rights remain appropriate and up-to-date. Conducting regular reviews helps organizations identify and address access issues in a timely manner, reducing the risk of security incidents and data breaches.
- Document Review Findings and Remediation Efforts: Document access review activities, findings, and remediation efforts to provide an audit trail and evidence of compliance with regulatory requirements. Documenting review activities helps organizations demonstrate accountability, transparency, and due diligence in access control management.
- Monitor and Audit Access Activity: Monitor user access activity and conduct periodic audits to assess the effectiveness of access controls and detect potential security risks or compliance violations. By monitoring access activity and auditing access logs, organizations can identify unauthorized access attempts, suspicious behavior, and potential security incidents.
Conclusion:
Ensuring compliance with regulatory requirements and maintaining robust data security are critical imperatives for organizations in today's digital landscape. User access reviews play a vital role in achieving these objectives by helping organizations identify and mitigate access risks, enforce segregation of duties, maintain compliance with regulatory requirements, and enhance incident response capabilities. By implementing best practices for conducting user access reviews and leveraging technology solutions, organizations can strengthen their overall security posture, protect sensitive data, and safeguard against emerging threats.
What's Your Reaction?











![Blog Submission Sites 2024 [High DA]](https://blognow.co.in/uploads/images/202306/image_100x75_6494a03eaff5e.jpg)
![Article Submission Sites 2023 [High DA & PA]](https://blognow.co.in/uploads/images/202307/image_100x75_64c4181f17036.jpg)
![Classified Submission Sites 2023 [High DA & PR]](https://blognow.co.in/uploads/images/202306/image_100x75_649dcd5260808.jpg)




![Article Submission Sites 2023 [High DA & PA]](https://blognow.co.in/uploads/images/202307/image_750x415_64c4181f08ed5.jpg)
![Classified Submission Sites 2023 [High DA & PR]](https://blognow.co.in/uploads/images/202306/image_750x415_649dcd5247eeb.jpg)
![Blog Submission Sites 2024 [High DA]](https://blognow.co.in/uploads/images/202306/image_750x415_6494a03e96bfa.jpg)